Security defaults in Azure Active Directory (Azure AD) make it easier to be secure and help protect your organization. Security defaults contain preconfigured security settings for common attacks such as password spray, replay, and phishing.
Microsoft is making security defaults available to everyone. The goal is to ensure that all organizations have a basic level of security enabled at no extra cost. You turn on security defaults in the Azure portal.
Note: If your tenant was created on or after October 22nd, 2019, it’s possible you are experiencing the new secure-by-default behavior and already have security defaults enabled in your tenant. In an effort to protect all of our users, security defaults is being rolled out to all new tenants created.
Deployment considerations
- Similar to security defaults, but with more granularity including user exclusions, Conditional Access will not be available while security defaults are enabled.
- Unified Multi-Factor Authentication registration
All users are required to register for MFA. - Protecting Administrators
Administrators are required to use MFA. - Protecting all users
All users are required to use MFA. - Blocking legacy authentication
Blocked Legacy Protocols include POP, IMAP, SMTP, Older Office Clients and ActiveSync using Basic authentication.
Note: App passwords are only available in per-user MFA with legacy authentication scenarios only if enabled by administrators - Protecting privileged actions
Accessing the Azure portal, Azure PowerShell, or the Azure CLI will require additional authentication. - Requiring Microsoft Authenticator app
The following authentication methods are not supported:- Call to Phone
- Text to Phone
- Verification code from mobile app or hardware token
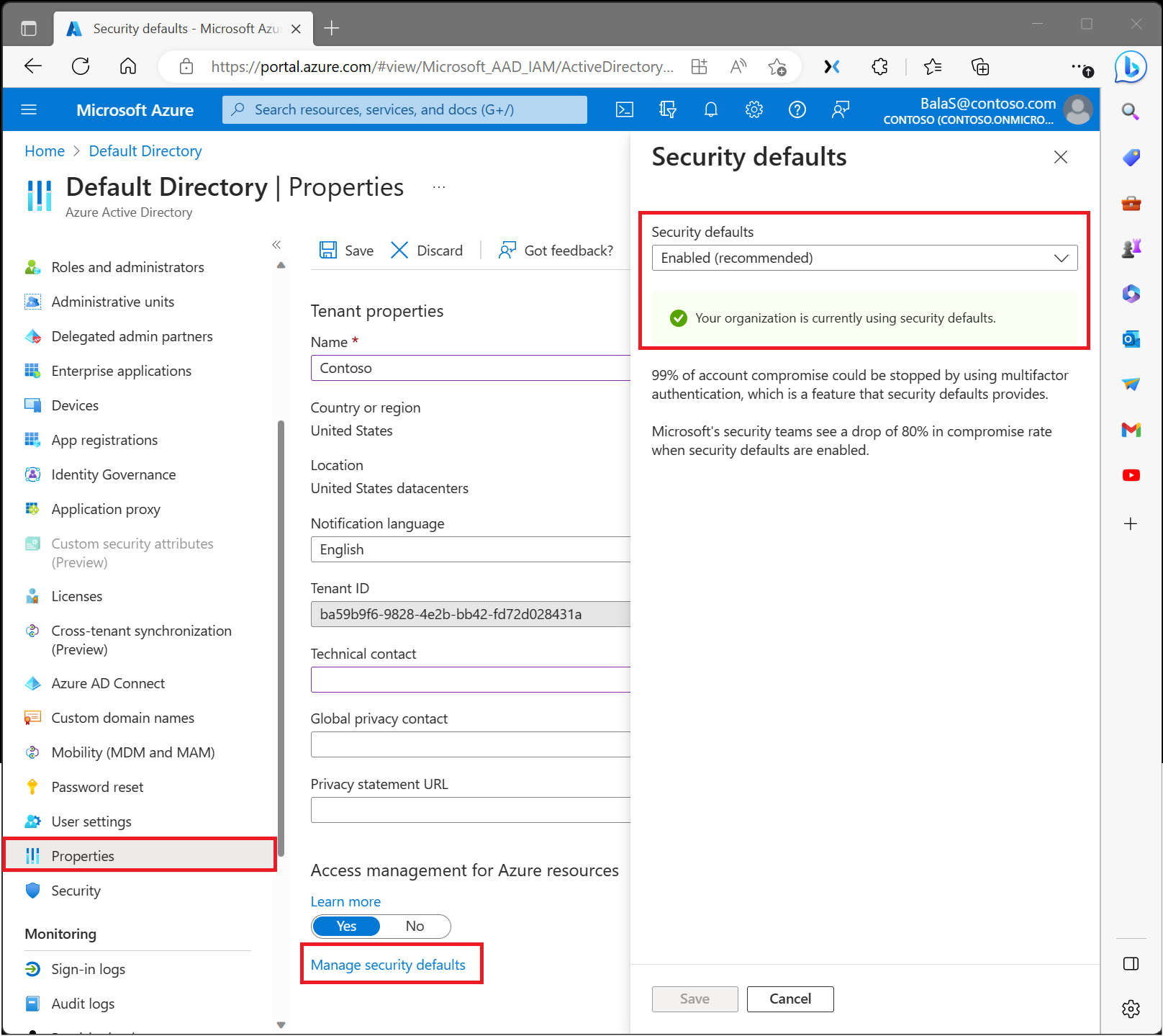
Enabling security defaults
- Sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
- Browse to Azure Active Directory > Properties.
- Select Manage security defaults.
- Set the Enable security defaults toggle to Yes.
- Select Save.
Disabling security defaults
Organizations that choose to implement Conditional Access policies that replace security defaults must disable security defaults.
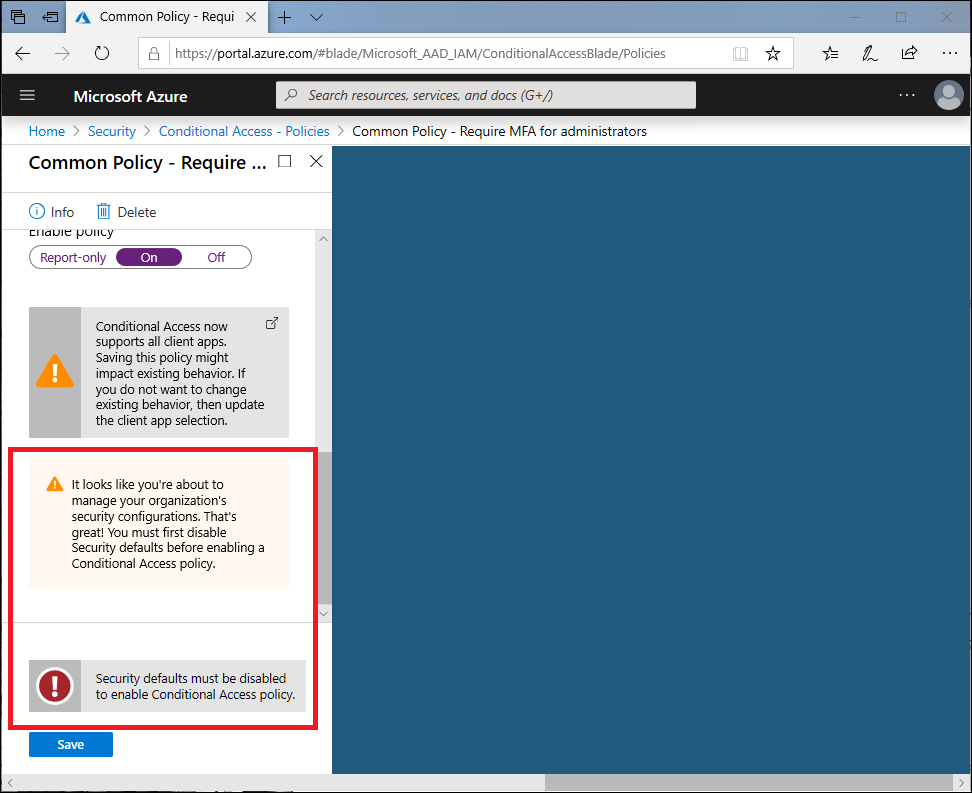
To disable security defaults in your directory:
- Sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
- Browse to Azure Active Directory > Properties.
- Select Manage security defaults.
- Set the Enable security defaults toggle to No.
- Select Save.
